Definitions and descriptions for key digital terminology
Most modern browsers have accessibility options which enable the viewing of websites for users who may be visually impaired, hard of hearing or effected by other ailments which may restrict their experience online.
The threat actor – the individual(s) or entities who pose a threat to a system. This can be either direct or indirect as a result of automation and pivoting.
Cyber Security intends to lower the risk of attackers successfully getting to your data and systems. You can deploy various tests both software driven and pen tested to asses your Web Application and systems security.
View the average percent watched on all views for the complete video. What percentage of your viewers have watched the entirety of your video? Can you make the content more compelling to engage your audience and increase the retention of viewers.
The search engine owned by Microsoft, having its routes with MSN and later Live Search. Bing offers services including Web, Image, Map and Video searches. Yahoo used the Bing search engine for its searches until 2015 when a deal meant that Yahoo only had to use Bing for the majority of it’s searches.

Bing Ads is another Pay Per Click platform for both the Bing and Yahoo! search engines. The features and designs are similar to that of Google AdWords, with a few of its own distinct features.

- Black Hat in relation to Internet Security refers to the unethical hacking or penetration of Websites. Black Hat hackers are unscrupulous hackers who violate computer security for little reason beyond malicious ends.
- Black Hat in relation to Search Engine Optimisation refers to the practice of gaining page rank in the search engines, but through violating the engines terms of service. Some examples are page stuffing, doorway pages and invisible text.
Blue Hat is used to describe the technique of hacking from people who are from outside the cyber security industry and are used for the testing of functionality on a web site.
BYOD (Bring Your Own Device) is a scheme where employees use devices which they own (such as mobiles and laptops) for work use.
This can go from companies which don’t wish to have the expense of issuing company phones to companies which allow employees to bring in tablets and laptops to use as their workstations.
BYOD does come with risks however – and not just the possibility of an employee using them as a time sink! There is always a risk of viruses or malware being spread by compromised BYOD machines onto a corporate network, along with other such abuses.
BOYD is best avoided if possible and is best mitigated by devices whether it be Smart Phones or Computers being purchased by the company and very good security attached to them.
A breach is the release of data from either a company or an individual.
This can be anything from a hacker breaking into your website to an employee leaving a USB or computer on a train. Employees should varying degree of access according their function within the organisation.
Disaster Recover Plan or Incident Recovery Plan aims to:
- See what was lost,
- Find out how it was lost,
- Make any announcements about the lost data,
- Ensure that it does not happen again.
Call to action overlays are triggered through either organic (unpaid) or paid ad and are free. They are literally what they are… overlays on the video pointing out a selling point or statement. Used in the correct way in Google and these are incredibly powerful adding an extra layer to your video by providing extra information. These call to action overlays can also positively effect your rankings if used in the correct way with your keywords.
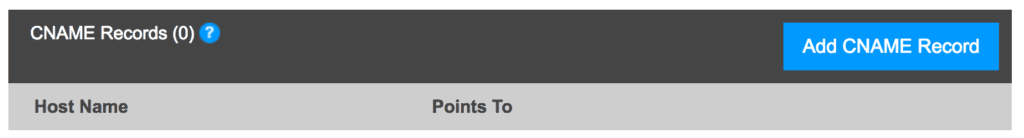
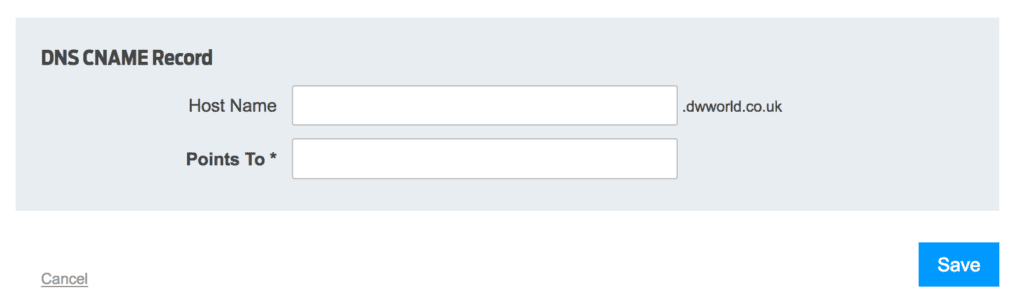
CNAME stands for ‘canonical name’ and it is a redirection to the targeted domain. It is basically used to assign a domain or sub-domain to another domain.
For example if you have yournamewebsite.com as your domain name and you are worried that people might spell it incorrectly such as placing an w in the URL address or spelling your name incorrectly. You can add these potential miss spellings to the CNAME records in the following way.
Easily done and could have a positive effect in extra traffic to your site.
The amount of expenditure on a particular ad in comparison to the all that companies AdWords spend.
The proportion of the estimated cost of buying the same number of visitors or (Through AdWords) for a term compared to the site coming to the site organically acquiring those visitors.
Average cost per view is the average amount an advertiser pays for a view of their video ad on YouTube. Cost per View can vary based on a number of factors including:
- Video ad length
- Video creative quality
- Customer Segment Targeting
- Dynamic Auction variables
Conversion Rate Optimisation is a combination of art, science and trial. Conversion Rate Optimisation is all about getting the maximum conversion rate from your online marketing efforts. Gaining an improvement in CRO is all about learning and tweaking, looking at your Google Analytics or Bing Analytic tools to review your data. Changing content, page layout, carrying out A/B tests adjusting PPC or Display adds may all affect your Conversion Rate Optimisation. What is important is that you carefully monitor your improvements, making notes of the adjustments made and the resultant change in your CRO.
It comes with practise and not achieved overnight. We have seen a simple change of imagery affecting the conversion rate.
The CTR or Click Through Rate is determined by the number of ‘Clicks’ on your advert divided by the number of Impressions or times that your advert has been shown.
10 (Clicks) / 1000 (Impressions) = 1 %
High Click Through Rates are a good indication that users find your advert useful and relevant. There are other benefits of high click through rates including a positive impact on your QTR or Quality Score. Increased quality scores can help reduce your advertising costs and in turn can also help increase your websites position.
The statistics available analytics tools breaking down viewers, or users split by age and gender. Target ads only to those who are more likely to be interested in your products or services e.g. 20-30 year old females. Highly recommended to target the exact target audience.
A disaster recovery plan is plan which states what to do in the event of a “disaster” – from a data breach of a website to flooding in the business premise..
It should state the best way to manage the IT systems of your business following a disaster – specifically, how to prevent such problems, how to identify potential issues, the steps to take when dealing with a disaster, and what to do following it.
A good example of a disaster recovery plan is at http://www.sans.org.
The Google Display network allows advertisers to use a combination of adverts to appear on Websites, in Videos or on mobile devices. The ads can be targeted to appear when the people who are likely to be most interested and on Websites most applicable. The Google Display Network can be targeted very specifically and is great for building brand awareness.
Your Domain Name Servers commonly known as DNS are the servers that host the information associated with your domain. They are registered to join the Domain Name System and will comprise of series of servers across the world.
When you purchase a domain the Domain Name Server will host all the necessary information to point to any other services that you will be using with that domain e.g. Website, Email services.
So typically your domain might be www.domainname.co.uk , com, .de or .london for example. Anything associated with that domain will be registered and controlled via a control panel on that DNS.
Once a domain is registered the registration details associated with the owner of that Domain will be stored in the Who IS register.
Typically a DNS will consist of the following formats:
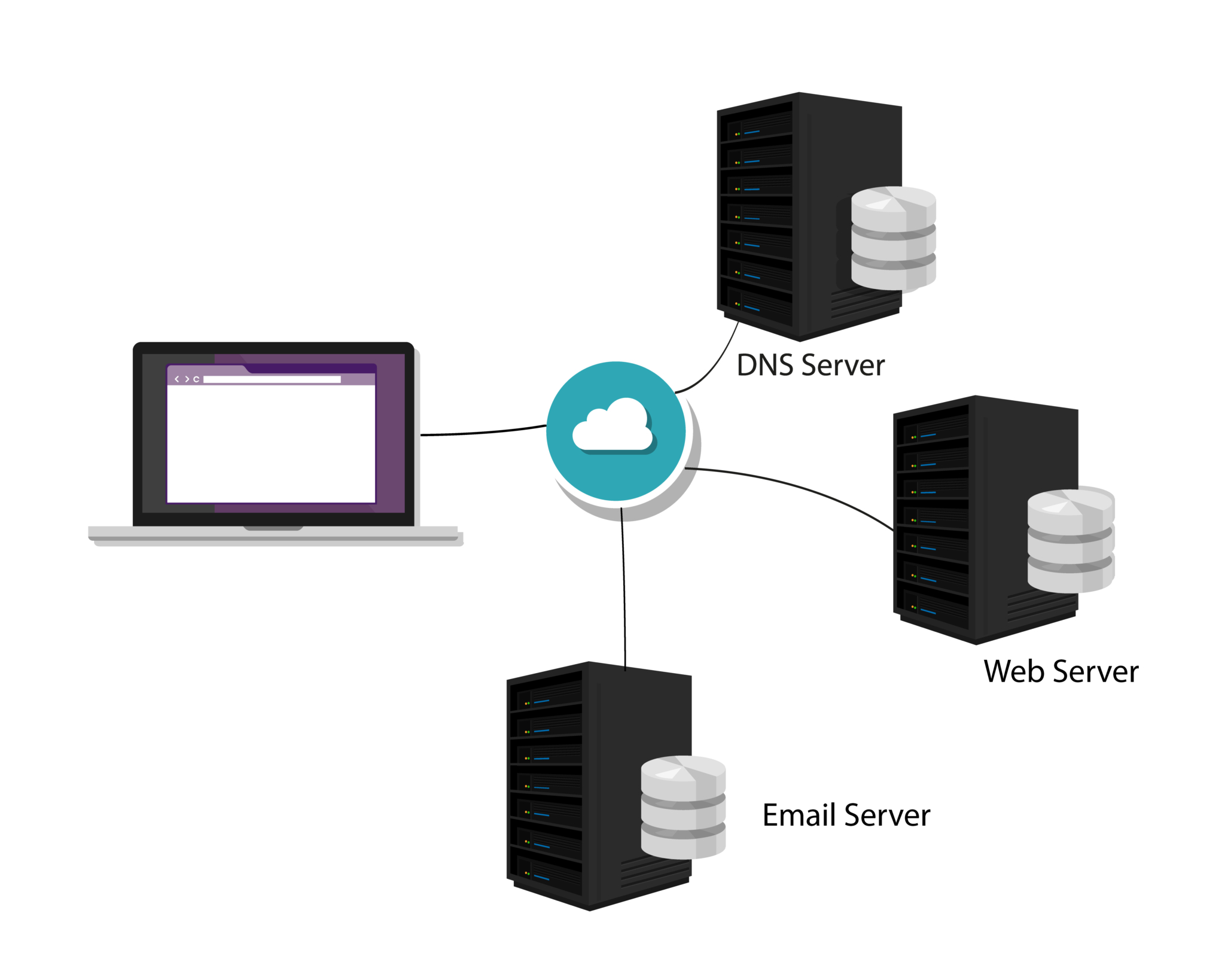
DNS Root Servers
DNS servers are organised in a hierarchy and at the very highest of the DNS servers are the aptly named DNS root servers. The DNS root servers store a database of all the Internet domain names.
Each domain name will have a corresponding IP address. There are 13 root servers named from A to M. These servers are deployed in the US, Japan, UK and Sweden.
How do DNS work?
The 13 root servers contain the complete database of names and addresses.
Other DNS servers are at a lower hierarchy and are maintained by organisations and Internet Service Providers (ISP’s). The DNS system works by the information being in a distributed format across the network of servers. Google and Amazon for example have their own DNS distributed around the world.
The architecture used in the DNS system is a client – server architecture. If you enter a search on your Firefox or Safari browser for example this issues requests to your internet service providers (ISP) DNS servers.
If that DNS server does not hold that piece of information it then passes that request onto another server. That DNS acting for the first client automatically passes that request to another DNS server or until the request eventually arrives at a DNS server that has the name and IP address in its database that matches. This information retrieved then passes all the way through the chain of DNS servers to the original client.
An exploit is a method which triggers a vulnerability. Thus exploitation is the process of using a systems weakness to gain access.
Exploits are often shared between various parties, either to improve a systems security, in order to stand as proofs on concept, or in order to break into a system for pride or profit.
Exploits are protected against at a software level with patches and updates (and can be sometimes protected by IDSs, firewalls, and other systems).
The popular search engine who’s name has become synonymous with search engines. Google was first formed in 1998 and for still a relatively young company leads everything to do with search on the web.

Google AdWords is an online advertising (PPC) service where you pay each time someone clicks on your ad. The system works by defining keywords you want your ads to be found by and writing compelling ad copy that entices a user to click-through.

Skewed Google search results that misleads the search engines in directing the user to a Website that does not match the search results. This is becoming increasingly harder to achieve as the Google search algorithms have become increasingly ‘intelligent’ at punishing the websites for trying to mislead the search engines.
The competitors that appear against your keywords that you are ranking for.
Estimated number of visitors coming from Googles search results.
Grey Hat hackers refers to the hackers that lie in between the Black Hat and the White Hat hackers by surfing the Web looking for websites that can be exploited. Following the hack they will either inform the owner of the hack and offer their services for correcting the hack or they will publish the hack to the world.
The Impression is the displaying of the advert – it is counted when the advert is effectively ‘fetched’ from its source. It is irrelevant of clicks and these are not counted. Impressions are open to Click Fraud and so there are a number of methods deployed to reduce the likely hood by the browsers employing various algorithms to reduce the robotic activity.
The deploying of illicit techniques to artificial view of websites without an intention to click through on the advert. The result is a reduction in the Click Through Rate and in so doing lower quality score. The lower quality score will significantly affect the advertisers ability to attain any discounts on its advertising spend.
A search on your Web Sites internal search tab allowing you to go direct to the subjects searched landing page.
Applications that allow you to view and access content (e.g. websites) shared with the World Wide Web.
An intrusion detection system is a system which “sits” between a system which is wanted to be protected and the outside world. It is able to detect the web traffic which passes to the protected system, and typically work out the intentions of said traffic. Installing an IDS can help to cut down spam, detect viruses, and log activity on a network.
It’s incredibly closely related brother, the Intrusion Prevention System, is an IDS which is able to act on what it finds, and either cut access or slow down the traffic.
What is the difference?
Two addressing standards for IP addresses are being used today. The new IPv6 standard is replacing the IPv4 32 bits addressing system. The older IPv4 addresses are 32 bits in length or 4 bytes. The IPv6 addresses are 16 bytes or 128 bits in length.
So what?
IPv4 address consists of a group of four numbers or bytes, each numbering between 0 and 255. Computers see just one number while humans see them as numbers or bytes separated by dots. So the numbering ranges from 0.0.0.0 to 255.255.255.255. The difference the new IPv6 numbering protocol uses hexadecimal numbers rather than decimal digits and the IPv6 uses colons as the separator between the hexadecimal numbers.
Words or phrases that describe your business, product or service that you choose to help determine how you rank on the search engines.
Keyword Research is the process of discovering for optimisation purposes based on different factors such as:
Search Volume – The number of searches each month for that term.
Keyword Difficulty – The difficulty to rank for a particular search term. The higher the % the more difficult it is.
Number Of Results – How many results appear in the SERPs based on the search term.
A landing page is simply the Page that the user is taken to when they click on your advert in either paid, display or organic search from the advert. The Landing Page has content which must be relevant to the text add, display add and have the appropriate Search Engine Optimisation techniques applied to the pages content.
The Landing Page will include the correct h1, h2, alt tags etc, the correct key words and meta tags applied. The images will also be Search Engine friendly. The written body of the page will be optimised in such a way to be search engine friendly which means the landing pages will have the appropriate keywords on the page and the density and distribution of the key words will be enough to be picked up as such by the search engines but not too many to invoke a spam alert.
Some more for the glossary will keep adding.
Malware is malicious software – programs which aim to damage or access systems which they are not permitted to do.
They can range from the merely annoying to the business destroying. Systems such as anti-virus and firewalls aim to stop malware, along with policies and procedures which aim to inhibit it’s effects.
Negative Keywords are crucial in that they help you not waste money. By deploying keywords you very quickly will maximise your return for your investment. The deployment of negative keywords are deployed when there are PPC words that are similar to another word or brand that could be confused with your keyword. Negative Keywords will prevent your advert from showing and will therefore result in more relevant results for your customers and in doing so will improve your quality score over time.
Packet sniffers are software tools that capture packets of data transferred over the internet and are used for viewing the passwords transferred in those packets. Also called Packet Analysers.
Internet Marketing Companies will typically manage a Real Time Bidding (RTB) campaign. RTB campaigns are typically a means by which advertising inventory is bought and sold on a per-impression basis. The RTB is a programmatic instantaneous auction very similar to those handled in financial markets.
With Real Time Bidding advertising buyers bid on an impression, if this bid is won then the buyer’s inventory ad is instantly displayed on the publisher’s site.
Real-time bidding lets advertisers manage and optimise adverts from different advertising networks by granting the advertisers access to a multitude of networks.
Real Time Bidding can be a highly effective way of launching campaigns and gaining extra reach in campaigns at exactly the right time with the exact audience they are wishing to target.
Usually hackers who use automated software tools written by other Black Hat hackers. The script referring to the fact they are using script developed by other black hat hackers. The Kiddie referring to the fact they have little knowledge of the underlying script that is being used.
Software that allows users to find content on the world wide web, based on the words or phrases typed in on the search engine.


The search string entered into the search engine to gain the results.
![]()
The number of results being displayed.
Site Audits are a scrutiny of your website – usually done by software tools with human analysis of the results. Site Audits can be purely an analysis of your website or can in comparison to an industry benchmark or competitor. Consider a Site Audit is as a equivalent of a GP’s Health Check. A Site Audit can be a simple software analysis of a Website looking at the Website health from an Organic Search Engine perspective, from a security perspective, or from a Paid Search perspective.
The site audit can help you prioritise what needs fixing first and in what order from site errors, to issues to warnings. Fixing priorities is very important for your rankings. You should carry out rankings on a regular basis to see how your website is progressively improving. The rankings over time will tell a story of how your work is progressing.
The site audit can be carried out from a security perspective and this can enable you to find all sorts of issues with your site.
We can track your various sites audits so you can know what has changed about your audit.
Small button on YouTube that enable the viewers to skip forward on the ad and not watch the video.
Spam refers to the ‘non targeted’ deployment of an email campaign, unsolicited emails, or gaining non genuine back linking to your site. It is very easy to get court with a Spam filter and end up being added to one. Back in the old days ‘early ‘000’s’ it was relatively easy to buy back links to your site. Google’s famous algorithms then moved to counter the unethical gathering of Backlinks to your site. Nowadays the search engines are fantastically good at spotting the unethically bad gathering of links and it really is not worth seeking and paying for back links that are not ‘naturally’ sourced.
Spamming also applies to email marketing also, and the relevancy of your email and we’ll it is structured are all determining factors in deciding if it considered Spam or not.
This is the comparison of a number of factors or variables on two or more website landing pages. The landing page or email are compared statistically based on the number of Click Through or other statistical variable measurement.
the, is, at, which, on…
Stop words are the words that some browsers remove from the search string and therefore are considered as redundant words or stop words. It can cause problems in phrase strings that use them as some search algorithms can remove them. The classic example is when searching for ‘the who’ where ‘the’ is removed from the search string completely changing the context of the search.
Generally when writing copy for tittles in both h1, h2 and other meta data it is advisable to remove the stop words.
The amount visitors and visits a website or web page receives.
True View video ads enable you to interactively engage with you customers on both YouTube and the wider web. You only pay with TrueView when a viewer watches 30 seconds of your video or the duration of the video if its shorter, or if they engage with any of the interactions such as the ‘Call to Action Overlays’ (CTA), clicking on cards and companion banners.
Video Remarking creates very specific lists based on viewer activity on your Tube account. With this list you can re-market or re-target as it is sometimes known.
A small snippet of code that is used to crawl Websites and is used to help reference or index for the search catalogues. Spiders also sometimes to referred to as bots.
- White Hat in reference to Internet Security is the use of White Hat techniques used by Ethical Hackers in their penetration tests of Websites.
- White Hat techniques in relation to Search Engine Optimisation are ethical techniques used in improving the rankings if a website.
WordPress is an open-source Content Management System. WordPress is run on a web server either externally or self-hosted via its WordPress.com service.
The CMS system is a template based platform where you can install themes and plugins (or WordPress’ own default editor) to help achieve desired effects and designs. WordPress is also compatible with the latest version of popular coding families such as HTML, CSS, PHP and many more.

Yahoo is a multinational tech company that is mainly known for its search engine Yahoo! Search and many other services online.

Synonyms of a word are words or phrases that have the same meaning. A synonym for digital marketing for example, is activities that are promotional or brand forming carried out online. If you use Synonyms in the copy you write it will help people understand your content better. This is especially true if you’re discussing difficult topics such as Marketing elements that people are unfamiliar with.
So synonym of a word are generally easier to understand than more complex technical terms. The use of Synonyms improves the readability of text and can help when you are writing lengths of copy where the same word could become repetitive. Googles’ algorithms can now pick up on the use of synonym’s in text blocks in many languages and so this also requires careful crafting.
The keyphrase in slug refers to how you have used your focus keyword or keyphrase in your URL. Your article or page should have an SEO-friendly URL and the ‘slug’ has the keyword included in this slug that sits at the end of your URL. To improve the slug part of your URL, we can build your keyphrases at the end of the URL so they maximise your opportunities to rank given all the other SEO factors affecting that page.
We'd Love To Hear From You!

Please do not hesitate to get into contact with us! We would love to discuss any requirements you may have. Either use the details below or the fill out the contact form to the right and we’ll get back to you as soon as possible.
1 Suite 4
Brighton
East Sussex
BN3 2HA
enquiries@dwworld.co.uk
01273 234688



Social Media are websites and apps that enable users to create, share and react to content posted by other users online. It also enables users to network with each other.
Some examples are Facebook, Twitter, Google+ & LinkedIn